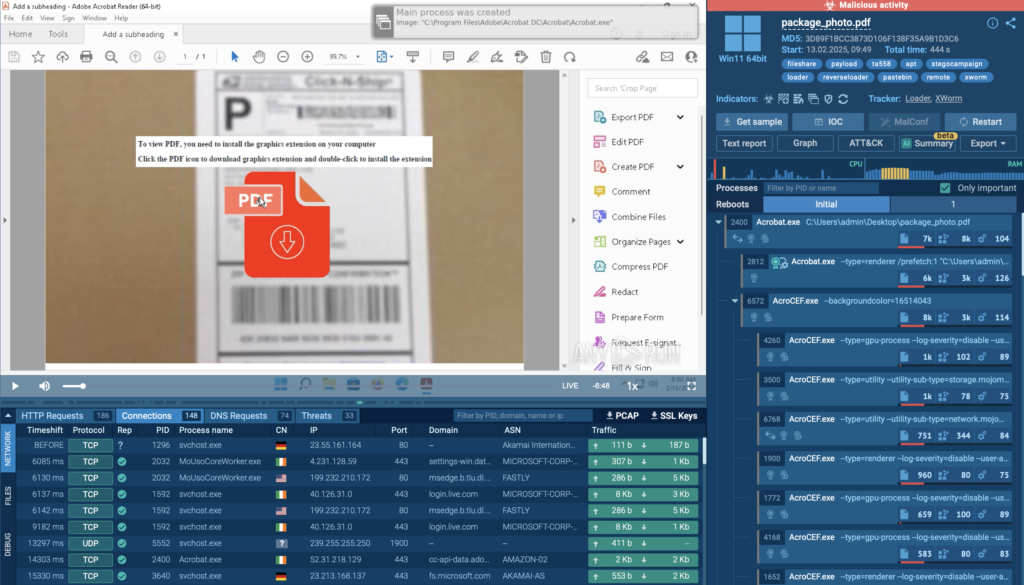
Cybercriminals continuously evolve their evasion techniques to bypass detection from security systems, making it increasingly difficult for security teams to respond to threats. This article examines common evasion tactics used by attackers, such as steganography, tool modification, and script obfuscation, detailing how these methods obscure malicious activities. Understanding these techniques is crucial for security teams to improve threat detection and response capabilities.
Affected: security teams, businesses, cybersecurity sector
Affected: security teams, businesses, cybersecurity sector
Keypoints :
- Cybercriminals refine evasion techniques to evade security measures.
- Evasion techniques are designed to hide malware and impede incident response.
- Keen understanding of these tactics aids quicker threat detection and mitigation.
- Real-world attack analysis within secure environments uncovers hidden threats.
- Strategies include disabling security tools, script obfuscation, and using trusted processes for malicious purposes.
MITRE Techniques :
- T1027.003 Steganography: Attacks utilize steganography to hide malware within innocuous images, avoiding detection by traditional security software.
- T1562.001 Disable or Modify Tools: Attackers modify Windows Defender by adding file extensions to its exclusion list, preventing detection of malicious files.
- T1140 Deobfuscate/Decode Files or Information: Attackers encode malicious payloads using Base64, which later get decoded on the victim’s system, allowing them to remain undetected.
- T1564.003 Hidden Window: Attackers execute PowerShell scripts with hidden windows to carry out malicious actions without raising user awareness.
- T1218.010 Regsvr32: Cybercriminals exploit Regsvr32.exe to execute malicious DLL files stealthily, enabling them to bypass detection methods.
Indicator of Compromise :
- [File] VideoSrcvbm.dll
- [Command] regsvr32 /s “C:Program Files (x86)ManyCamBinVideoSrcvbm.dll”
- [Command] powershell.exe -NoProfile -ExecutionPolicy Bypass -Command “”
Full Story: https://any.run/cybersecurity-blog/cybersecurity-blog/five-common-malware-evasion-techniques/
Views: 37