Threat Actor: Cybercriminals
Victim: Individuals and businesses
Information:
– There are 31 new variants of ransomware identified in March.
– Ransomware encrypts valuable data on infected systems.
– Cybercriminals demand exorbitant ransoms for decryption keys.
– Ransomware poses a significant threat to individuals and businesses.
– Detection and mitigation of ransomware are increasingly challenging.
– Ransomware jeopardizes the integrity of personal and sensitive data.
– Ransomware imposes substantial financial burdens on victims.
– Each new variant of ransomware refines cybercriminals’ tactics.
– Ransomware is characterized by its insidious nature.
– Ransomware holds critical information hostage.
– Ransomware is a nefarious practice.
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
**************************************************
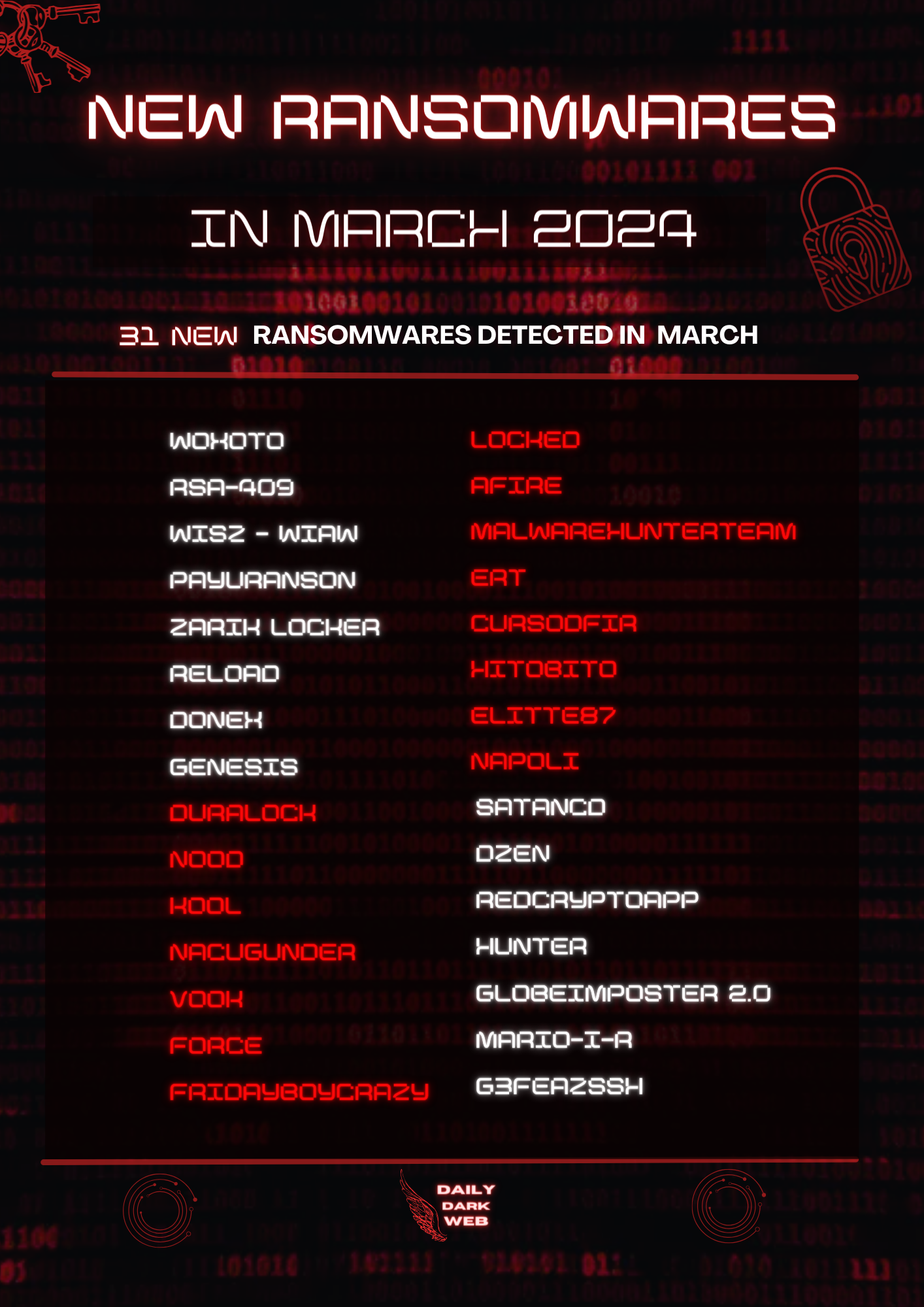
In March, cybersecurity experts have identified of 31 new variants of ransomware. These malicious programs, characterized by their insidious nature, pose a significant threat to individuals and businesses alike. With each new variant, cybercriminals are refining their tactics, making detection and mitigation increasingly challenging. Ransomware operates by encrypting valuable data on infected systems, rendering it inaccessible to users. Subsequently, the perpetrators demand exorbitant ransoms for the decryption keys, effectively holding critical information hostage. This nefarious practice not only jeopardizes the integrity of personal and sensitive data but also imposes substantial financial burdens on victims.
- WoXoTo
- SHA-256: 71dcf6d8418969549dcbd946ff93d713a4f4f89292f109ba9ba064d1b96b29ff
- Extensions: .WoXoTo
- RSA-4096
- SHA-256: 7a609187c615cd3209d6911824217d08a5c8bfacfbdaf9b4cdbaf6ed3f56f2d0
- Extensions: .RSA-4096
- Wisz – Wiaw
- SHA-256: 7a609187c615cd3209d6911824217d08a5c8bfacfbdaf9b4cdbaf6ed3f56f2d0,
- SHA-256: 557ece892da38340d69ed65ac32d1fe4f714643342dedbcbb166e5f334d82311
- Extensions: .wisz – .wiaw
- Payuranson
- SHA-256: 00b93b6037537b7119361ca2a4a9641abc8d8f9fd182c6804859e12c2e391e88
- SHA-256: 486f2eb64908f44b45220dd70aba4f6aacdf5208282c654d5ecb028b7ab8d1cd
- Extensions: .payuransom
- Zarik Locker
- SHA-256: 7a609187c615cd3209d6911824217d08a5c8bfacfbdaf9b4cdbaf6ed3f56f2d0
- Extensions: .zarik5313
- Reload
- SHA-256: 4bf91340c43770c365d14c23181f77c7539d0a6151b2fd18302944aa12e0d7c6
- Extensions: .reload
- DoNex
- SHA-256: 0adde4246aaa9fb3964d1d6cf3c29b1b13074015b250eb8e5591339f92e1e3ca
- Extensions: Victim’s ID
- Genesis
- SHA-256: 09b1e725a155fad0c058b17557dcb9008632816db5151f2d417c8fc6b7b7a9de
- Extensions: .genesis15
- Duralock
- SHA-256: 91d225be3b1252c1454f8020ad4abea4a948d44b69ef15735aabcce06001c948
- Extensions: .duralock05
- Nood
- SHA-256: 9f24cff00ff55730e61d9fd9a182f92f272735ba6ce55bc93bdc7ea24424dc42
- Extensions: .nood
- Kool
- SHA-256: ac306e0ac7d13ecf338be79b04e8cdb6c6d796e2f56c02a535125276ee058d9d
- Extensions: .kool
- Nacugunder
- SHA-256: df60925da9cd35a145504c5da31be67d95bcf00c464c53070d89867a272ab71a
- Extensions: .nacugunder
- Vook
- SHA-256: b90d1767ecd240187bf3814f38b22a6254f72b89d046c99c9f1a6b7aa6a5d4f5
- Extensions: .vook
- FORCE
- SHA-256: 9cdb868940c8de8f7699797d7a3bc7eece989a7ac2bebead885bc02526522b45
- Extensions: .FORCE[ID]
- FridayBoycrazy
- SHA-256: 3488e674a734e33410a122472c102763edb84b4184b10e041f9c774b9213bd22
- Extensions: 4 random characters
- Locked
- SHA-256: 10a3fc2cdb4f7f7bb7fd4af1bce19e9c9cf064dff9929e18e0cdc53879d90ebe
- Extensions: .locked9
- Afire
- SHA-256: 3656c44fd59366700f9182278faf2b6b94f0827f62a8aac14f64b987141bb69b
- Extensions: .afire
- MalwareHunterTeam
- SHA-256: 9012a3958219ec427b9b447dffca591b19cb4097f3bb89acc1389c4da59f6dfe
- Extensions: .malwarehunterteam
- Ert
- SHA-256: 4a8e0a54a6c46c807c36900764b7f134b755be5f45aca496b803d2fbfe25f93b
- Extensions: .ert
- cursoDFIR
- SHA-256: 24266d8af5e54a179ca62fe8ba586a9bced5e39565ad05f33583a3fc8f509613
- Extensions: .cursoDFIR
- Hitobito
- SHA-256: 1940fcdb2561c2f7b82f6c44d22a9906e5ffec2438d5dadfe88d1608f5f03c33
- Extensions: .hitobito
- ELITTE87
- SHA-256: 0f5463f9c8e4a71be6d1ed05b687632dc6fb121f250e2370a69815ef20518bfd
- Extensions: .ELITTE87
- Napoli
- SHA-256: 13098492245fd60ce685a0050eaa0a5105d6841cbb3e042e99b1020cbe3b4bfc
- Extensions: .napoli
- SatanCD
- SHA-256: f813c628d489e6da2a57ac1ef6c4152382f810ffe3e19ac2c296c7a26b5a6a99
- Extensions: random characters
- Dzen
- SHA-256: 2276fe3cc324c9e053eea9839874963a27f312dcf01b97d298e5d326a7c12b87
- Extensions: .dzen
- REDCryptoApp
- SHA-256: 6fe20b1b2ab6f8f614ae0e9ed94c2728f0d6b297
- Extensions: .REDCryptoApp
- HUNTER
- SHA-256: 87b6b5d5054753bafd2c8e64ba222f0590a16916b82ce901cce83f0e834707b1
- Extensions: .HUNTER
Source: Original Post