
In its 2023 Adversary Infrastructure report, Insikt Groups outlook for the infrastructure landscape in 2024 suggests a continuation of the evolving nature of cyber threats, with an emphasis on government efforts to combat malicious activities. Anticipated increases in takedowns of malicious infrastructure reflect a growing awareness among governments of the devastating impacts of ransomware and other destructive attacks. There is a specific focus on cybercriminal operations affecting critical infrastructure, such as hospitals, prompting governments to explore legal frameworks for actions against attackers.
While takedowns prove effective, the persistence of criminal organizations, exemplified by ongoing operations like TA577 after the QakBot takedown, highlights the need for apprehending individuals responsible for illicit activities to truly disrupt such operations.
The shift of advanced persistent threats (APTs) towards adopting commodity tools, especially command-and-control (C2) frameworks, is expected to continue, as these tools effectively obscure attribution. Additionally, all threat actors are likely to exploit remote monitoring and management software, such as AnyDesk and ConnectWise, along with legitimate internet infrastructure like Telegram and GitHub, capitalizing on perceived legitimacy and inadequate network controls.
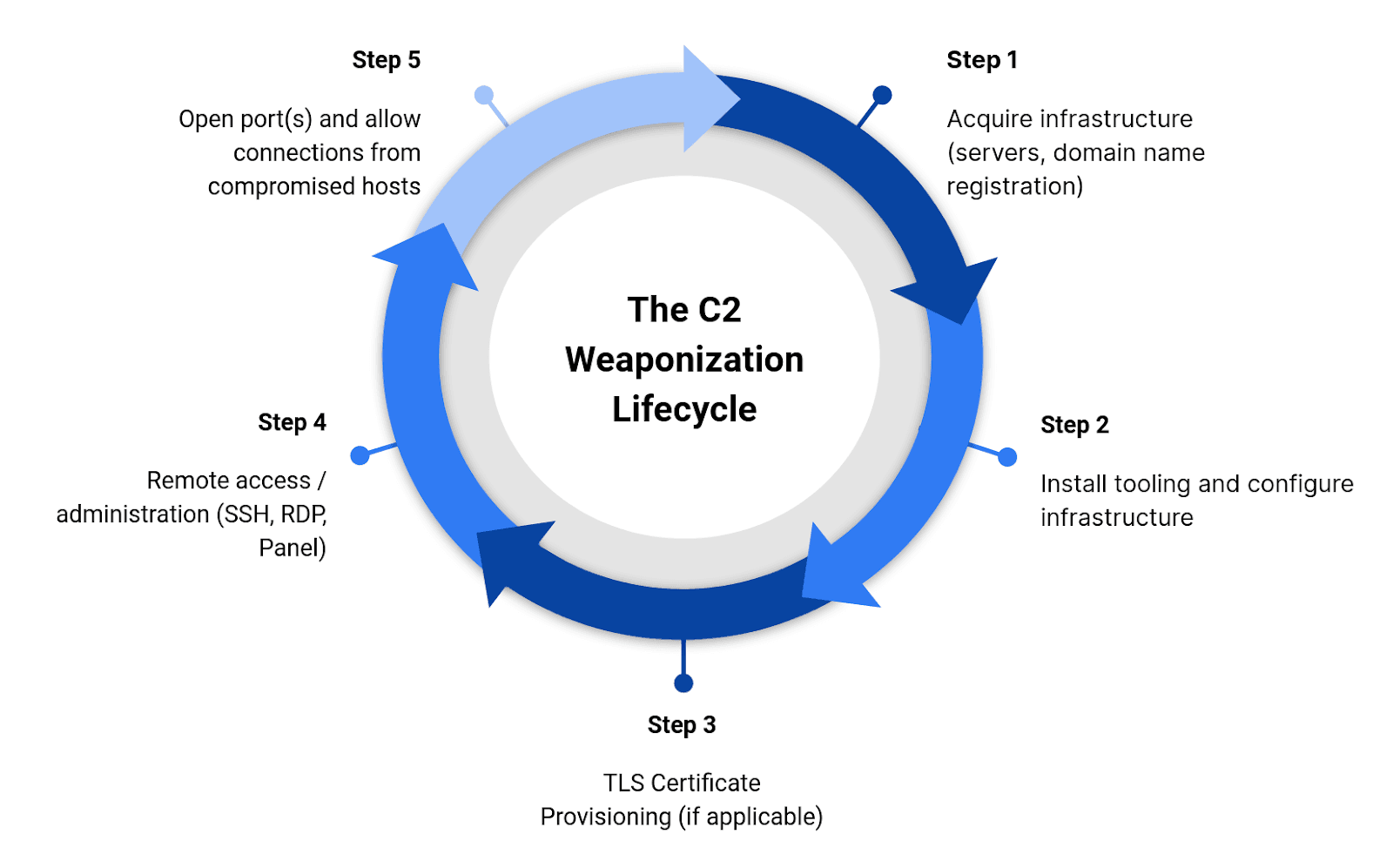 C2 weaponization lifecycle (Source: Recorded Future)
C2 weaponization lifecycle (Source: Recorded Future)
Artificial intelligence (AI) is foreseen to impact cybercrime incrementally in 2024, particularly in areas like domain naming, network planning, and advanced obfuscation techniques for malware development. The use of AI by threat actors is expected to enhance organizational and technical efficiencies, reduce entry barriers for sophisticated attacks, and offer advantages to cybercriminals.
The report also identifies top offensive security tools, including Cobalt Strike, Viper, and Meterpreter, as well as prominent remote access tools (RATs) like AsyncRAT, QuasarRAT, PlugX, ShadowPad, and DarkComet. Sharing this information is encouraged to aid others in evaluating threat models, allowing for data verification by researchers and fostering a comprehensive understanding of the malicious infrastructure landscape.
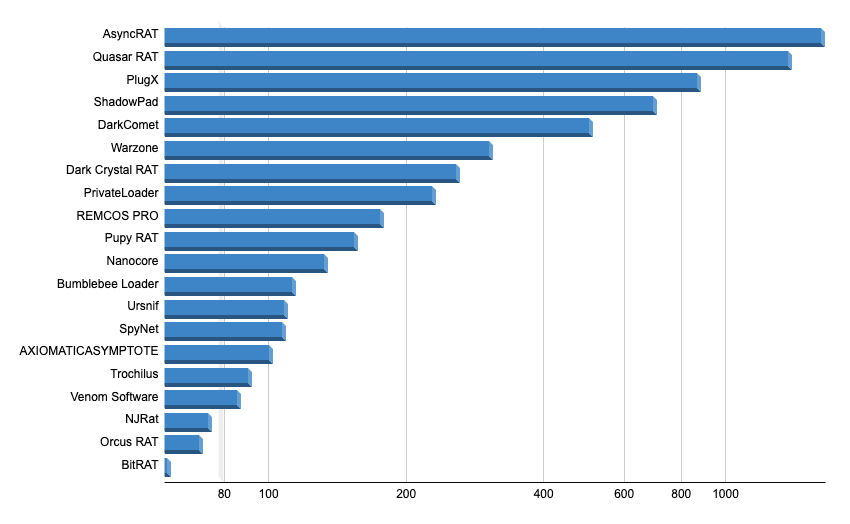 Top 20 RATs and backdoors, based on the number of unique C2 servers observed (Source: Recorded Future)
Top 20 RATs and backdoors, based on the number of unique C2 servers observed (Source: Recorded Future)
In response to emerging threats, the report recommends organizations establish baselines for legitimate internet services on their networks and optimize security controls. However, it acknowledges that advanced security measures, such as decrypting and monitoring TLS traffic, may be necessary, necessitating careful consideration of privacy implications, implementation costs, and potential impacts on network systems and productivity.
To read the entire analysis, click here to download the report as a PDF.
Source: Original Post
Views: 0