This blog explains how to detect SQL injection vulnerabilities in an Android app’s content provider using Drozer. Content providers manage app data and control access to it, allowing secure interactions with data. The article provides a step-by-step guide for exploiting these vulnerabilities to gain unauthorized access to data. Affected: Android applications
Keypoints :
- Introduction to Drozer as a tool for exploiting SQL injection vulnerabilities in Android apps.
- Content providers in Android manage access to a variety of data types.
- Data operations that can be performed through content providers include creation, reading, updating, and deletion.
- Steps to identify the target application package name for further exploitation.
- Using Drozer to verify attack surfaces and gather information about content providers.
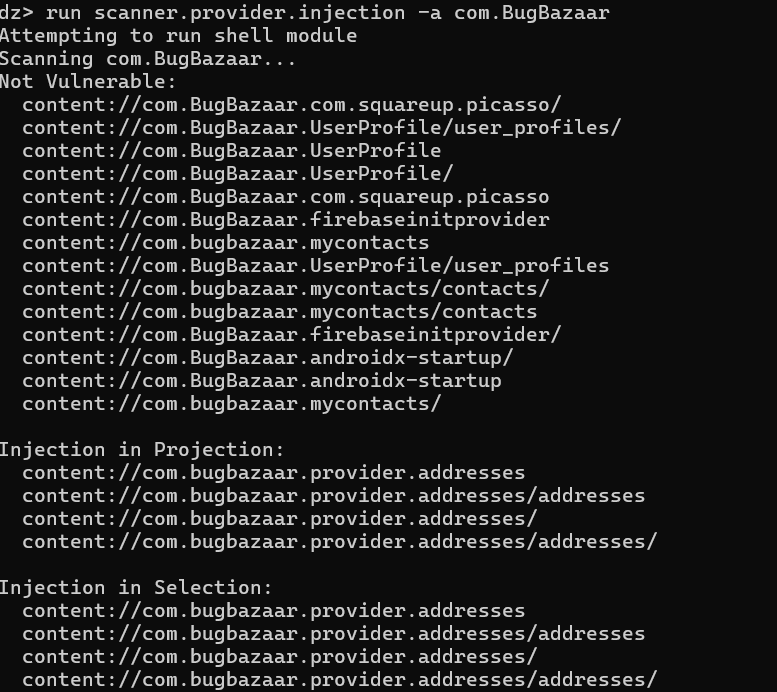
- Techniques for scanning accessible URIs that could be vulnerable to SQL injection.
- Understanding SQL concepts such as projection and selection necessary for exploiting vulnerabilities.
- Steps to check for SQL injection within accessible URIs and confirm database errors.
- Methods to identify table names and dump data from vulnerable databases.
- Instructions on how to insert and delete data from the database through content providers.
- Encouragement to participate in bug bounty programs for financial rewards.
- Recommendations for mitigating vulnerabilities, including using permissions and parameterized queries.